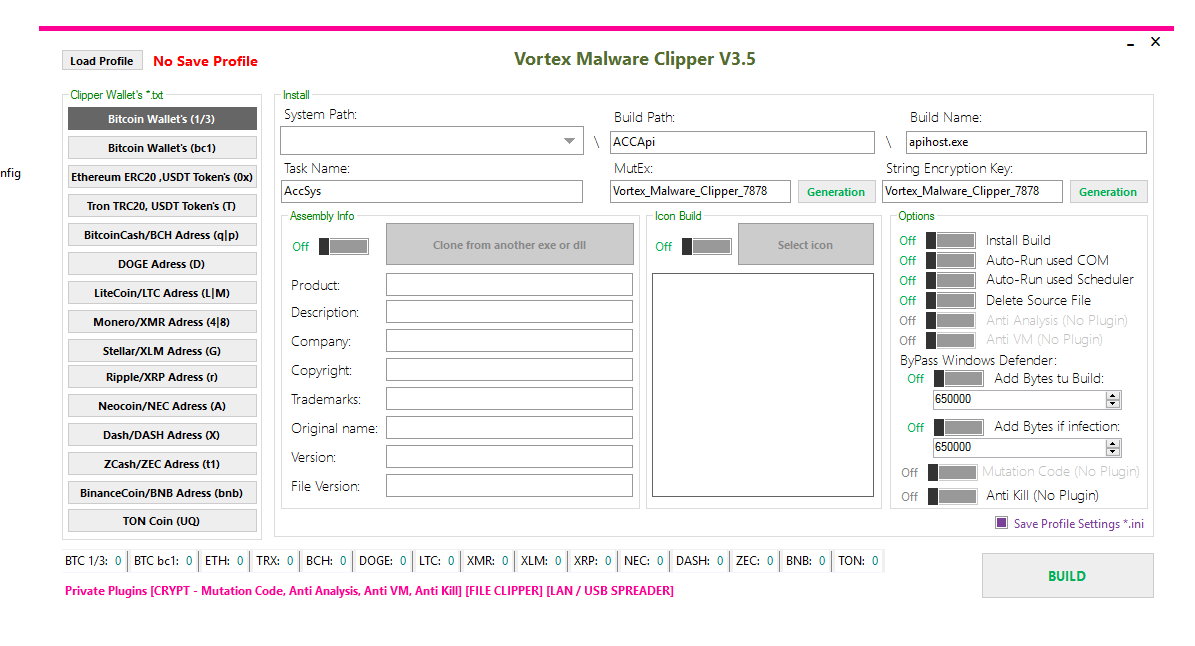
Destiny Stealer 2026: Technical Overview, Capabilities, and Cybersecurity Implications
Introduction to Destiny Stealer 2026
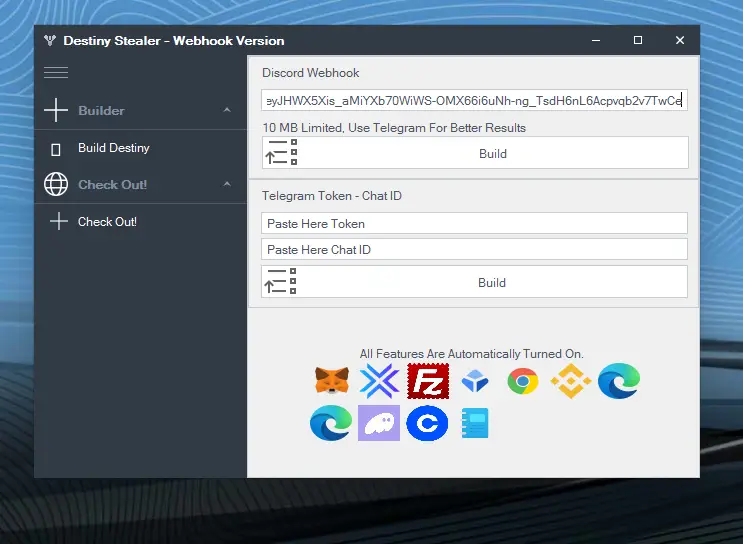
Destiny Stealer 2026 is a publicly available open-source project hosted on GitHub under the Destiny-Team organization. The software is categorized as an information-stealing malware framework, commonly referred to in cybersecurity research as a stealer.
This article is written strictly for educational, defensive, and research purposes, aiming to help cybersecurity professionals, students, and analysts understand how such threats operate and how they can be detected and mitigated.
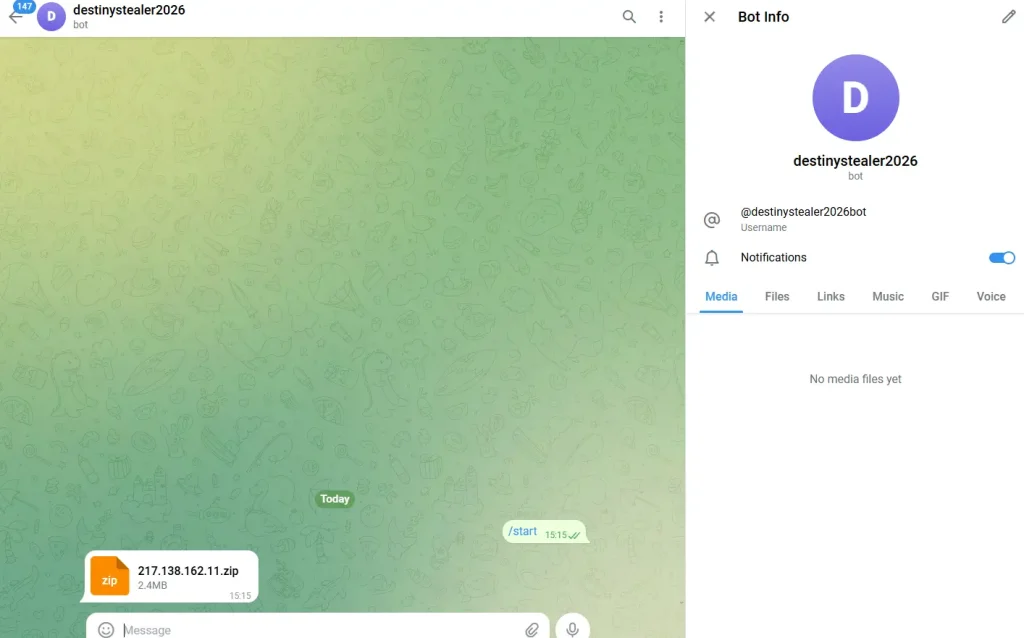
With the rise of credential theft attacks in recent years, projects like Destiny Stealer 2026 are often analyzed to improve malware detection, endpoint security, and threat intelligence systems.
What Is Destiny Stealer?
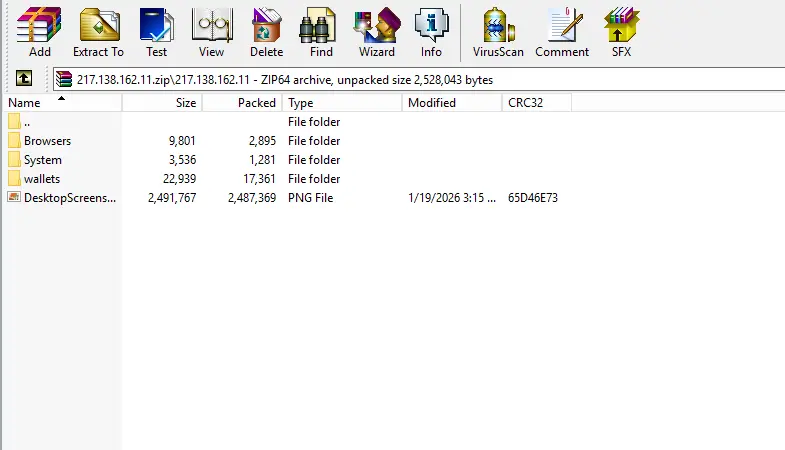
Destiny Stealer is designed to extract sensitive data from infected systems, typically targeting:
- Stored browser credentials
- Cookies and session tokens
- Autofill data
- System information
- Application-specific data
Such malware is frequently studied by security researchers to understand modern attack vectors, data exfiltration techniques, and obfuscation methods used in real-world cybercrime.
Core Functional Capabilities
1. Credential Harvesting Mechanism
Destiny Stealer 2026 demonstrates how modern stealers interact with browsers and local storage to retrieve saved login credentials. This behavior highlights why password managers and encrypted storage are essential in modern computing environments.
2. Browser Data Extraction
The software includes routines capable of collecting browser-based data such as cookies, history, and saved sessions. From a defensive perspective, this emphasizes the importance of browser sandboxing and endpoint monitoring.
3. System Profiling
Destiny Stealer gathers system metadata, including:
- Operating system details
- Hardware identifiers
- Installed applications
System profiling allows attackers to evaluate the value of compromised machines, a technique commonly documented in malware research.
4. Modular Architecture
One notable aspect of Destiny Stealer 2026 is its modular design, allowing researchers to observe how stealer malware can be extended or customized. This modularity is a critical topic in malware reverse engineering and threat modeling.
Technical Architecture Overview
From an analytical standpoint, Destiny Stealer 2026 provides insight into:
- Payload execution flow
- Data collection pipelines
- Local file system interaction
- Network-based data exfiltration concepts
Understanding this architecture helps security teams design better intrusion detection systems (IDS) and endpoint detection and response (EDR) rules.
Why Destiny Stealer 2026 Matters for Cybersecurity Research
Studying open-source malware projects like Destiny Stealer 2026 allows defenders to:
- Improve malware signature detection
- Train behavioral analysis engines
- Develop sandboxing and isolation strategies
- Educate students on real-world threat models
Rather than enabling misuse, responsible analysis strengthens overall cybersecurity resilience.
Legal and Ethical Considerations
It is crucial to emphasize that unauthorized use, deployment, or modification of stealer malware is illegal and unethical in most jurisdictions. Destiny Stealer 2026 should only be examined in:
- Controlled lab environments
- Academic research
- Malware analysis sandboxes
Ethical cybersecurity research focuses on defense, prevention, and awareness, not exploitation.
Defensive Strategies Against Stealer Malware
To protect systems from threats similar to Destiny Stealer 2026, organizations and individuals should implement:
- Updated antivirus and EDR solutions
- Regular OS and browser updates
- Strong password hygiene and MFA
- Limited user privileges
- Network traffic monitoring
These measures significantly reduce the effectiveness of information-stealing malware.
Download Destiny Stealer 2026
Conclusion
Destiny Stealer 2026 serves as a valuable case study in modern stealer malware design. When analyzed responsibly, it helps cybersecurity professionals better understand credential theft techniques and reinforces the importance of proactive digital security practices.
Educational analysis of such projects contributes to safer systems, stronger defenses, and a more informed cybersecurity community.