Black Flag XMR Miner 2026 has appeared in security briefings and threat reports as a stealthy cryptocurrency miner marketed with a suite of evasion and resilience features. This article provides a neutral, defender-focused analysis of the miner’s advertised capabilities, associated risks to organizations, indicators of compromise (IOCs) to monitor, and practical mitigation and incident-response recommendations for IT and security teams.
What is Black Flag XMR Miner 2026?
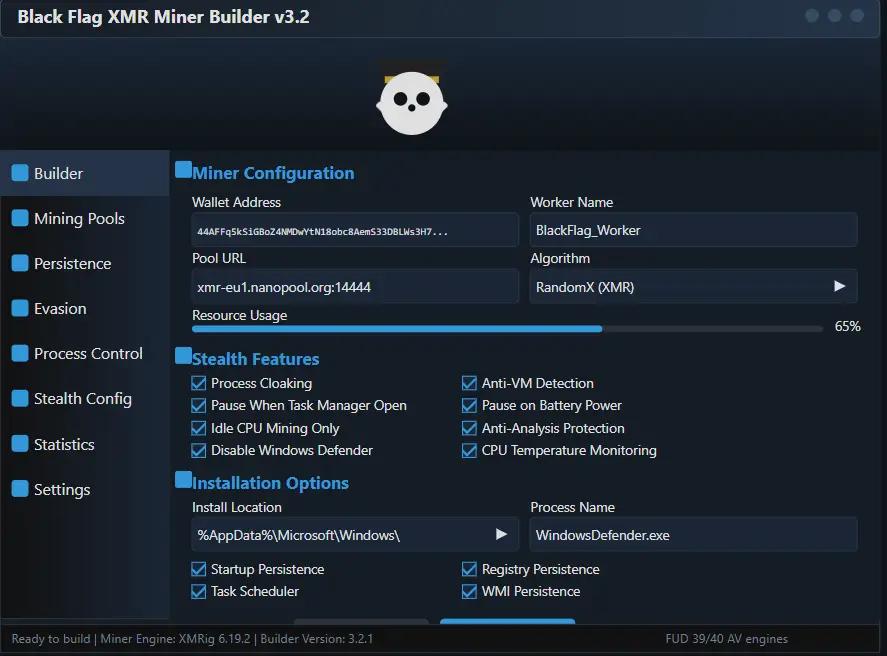
Black Flag XMR Miner 2026 is described in underground forums and security advisories as a professional-grade Monero (XMR) mining payload that prioritizes stealth and persistence. While researchers debate the origin and distribution vectors, defenders should treat any miner with these characteristics as cryptojacking malware and act accordingly to protect systems and network resources.
Advertised capabilities (high-level)
According to reports and sample descriptions shared with analysts, the miner is associated with — or claimed to include — the following capabilities (presented here purely for defensive awareness):
- Silent XMR mining (aimed at low CPU visibility)
- Compiled crypter to evade detection
- SSL/TLS support for encrypted communications
- Domain fallback support for command-and-control resilience
- Watchdog that restarts the miner if it stops
- Memory injection to avoid writing payloads to disk
- “Process watch” to pause mining when specific user processes run
- On-the-fly configuration updates
- Integration with XMRig proxy setups
Note: This list is included for defender awareness. No operational instructions or step-by-step guidance are provided.
Why this is dangerous for organizations
Cryptomining malware like Black Flag XMR Miner 2026 creates tangible harms:
- Resource drainage: High CPU/GPU consumption increases power usage and degrades system performance.
- Operational impact: Critical applications and services can slow or fail when host resources are saturated.
- Security risk: Presence of stealthy malware indicates a compromise and potential lateral movement or additional payloads.
- Cost and reputation: Increased energy bills and the potential exposure of customer or corporate systems.
Indicators of compromise (defensive, high-level)
Security teams should monitor for behavioral signs rather than rely exclusively on signatures:
- Unexplained CPU/GPU utilization spikes on otherwise idle hosts.
- Unusual outbound network connections to atypical domains, especially over encrypted channels.
- Repeated process restarts or watchdog-like behavior observed in system telemetry.
- Instances where legitimate startup persistence has been modified or unusual memory-only processes appear in telemetry (investigate cautiously and legally).
- Alerts from endpoint detection platforms indicating memory-resident threats or obfuscated binaries.
Avoid acting on a single indicator; combine multiple signals and follow incident-response playbooks.
Detection strategies (non-actionable, high-level)
To strengthen detection posture:
- Ensure EDR/antivirus solutions are up-to-date and tuned to detect memory-resident threats and obfuscated binaries.
- Monitor system performance baselines and raise alerts for sustained deviations.
- Centralize logs (endpoint, network, and proxy) to correlate anomalous activity.
- Employ network egress monitoring to identify suspicious encrypted connections or unknown domain resolution patterns.
These are defender-focused approaches — not operational instructions for attackers.
Mitigation and containment recommendations
If you suspect a cryptominer infection:
- Isolate affected hosts from the network to prevent lateral movement.
- Collect forensic artifacts (logs, memory images) for analysis by your security team or an external incident response provider.
- Restore from known-good backups after thorough cleansing and validation.
- Patch and harden exposed services and credentials to prevent re-infection.
- Review ingress vectors (phishing, unsecured RDP, exposed services) and remediate accordingly.
Engage legal and compliance teams as needed; cryptojacking incidents can have regulatory implications.
Hardening & long-term prevention
- Enforce least privilege and MFA for remote access.
- Restrict execution of unsigned or unexpected binaries by application control.
- Maintain up-to-date vulnerability management and patching cycles.
- Use network segmentation to limit access between user endpoints and critical infrastructure.
- Train staff on phishing risks and suspicious downloads.
Incident response playbook (summary)
A short IR checklist:
- Triage and confirm scope.
- Contain affected systems.
- Preserve evidence for analysis.
- Remediate, rebuild, and validate systems.
- Notify stakeholders and review controls to prevent recurrence.
FAQs (SEO-friendly, defensive)
Q: Is Black Flag XMR Miner 2026 a legal mining tool?
A: Tools advertised with stealth, memory injection, or crypters are commonly used for unauthorized cryptomining and are associated with malicious activity. Use only legal, transparent mining solutions on systems you control.
Q: How can I tell if my server has been cryptomined?
A: Look for sustained unusual CPU/GPU usage, degraded performance, and odd outbound connections—then follow your incident response process to investigate.
Q: Can antivirus detect memory-resident miners?
A: Modern EDR solutions are better equipped to detect fileless and memory-resident threats, but detection efficacy varies. Layered defenses and centralized logging help improve visibility.
Conclusion
Black Flag XMR Miner 2026 — as described in various security discussions — demonstrates the continued evolution of cryptojacking threats. Organizations should treat such tools as serious threats, prioritize detection and hardening, and maintain a robust incident response capability. If you suspect an infection, follow established IR protocols and consider engaging experienced security responders.